User Impersonation
User impersonation is a very powerful tool that allows you to get an exact look at what a particular user sees when they use your product. This can be helpful for anything from debugging issues to giving a realistic sales demo.
Turning on User Impersonation
The User Impersonation settings can be found under User Impersonation in the dashboard. Note that you must have the Owner role for your Organization in PropelAuth in order to access it, and you must be on a paid plan to enable it.
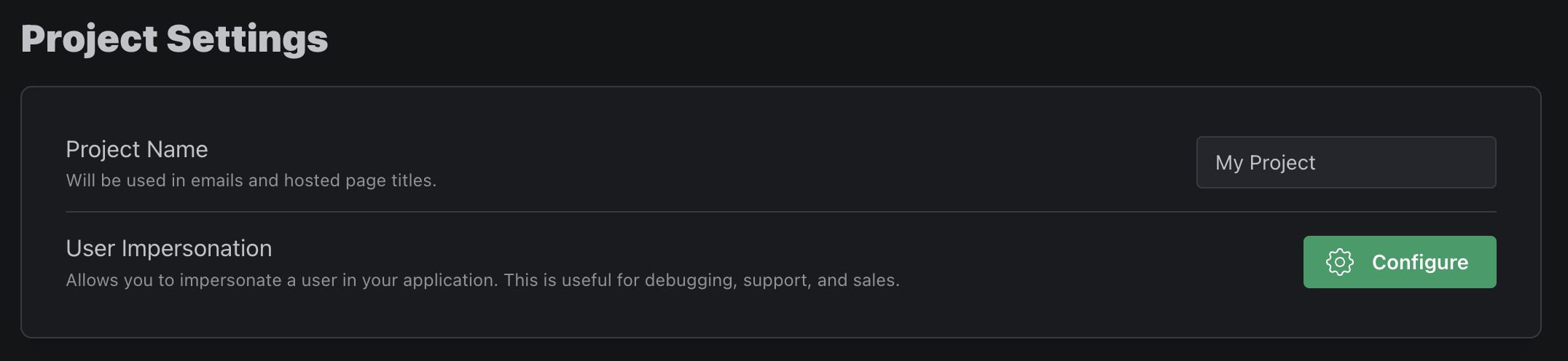
Setting Impersonators
Project Owners have the ability to set who can and cannot impersonate users in your application. Due to it's potential sensitive nature, we recommend giving the minimum amount of access necessary.
Owners can also choose which project members require approval to impersonate users as well as who can approve the requests.
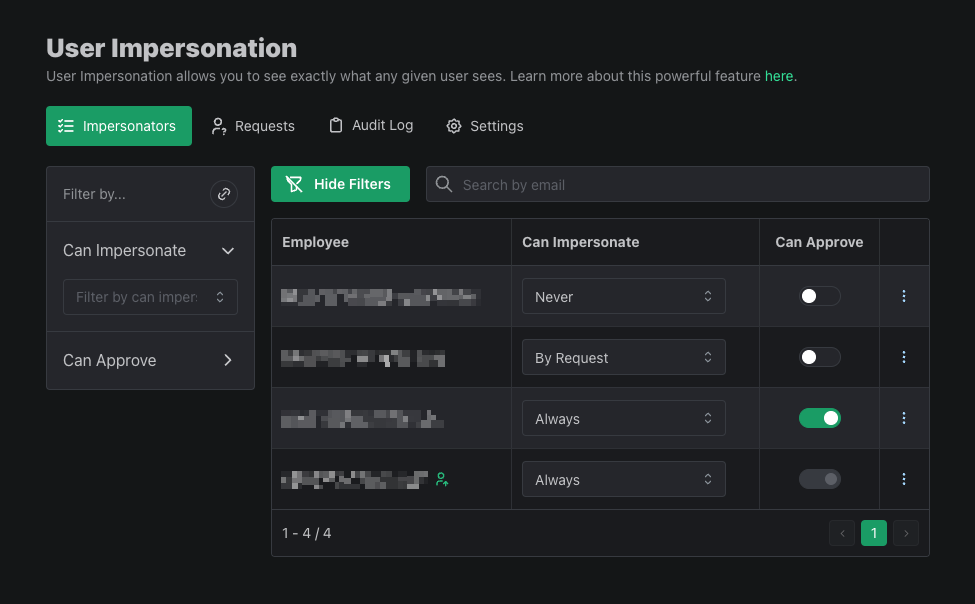
Impersonation Requests
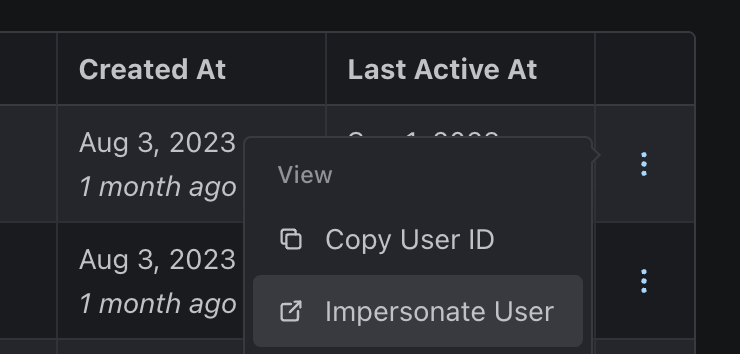
Members who have the "By Request" impersonation setting will have to submit a request for approval before impersonating a user. They can make a request by navigating to the Users table in the dashboard, locating a user in the table, and clicking the 3 dots at the end of the row.
The impersonation request form includes a duration of how long the member will be able to impersonate the user as well as a reason for the request.
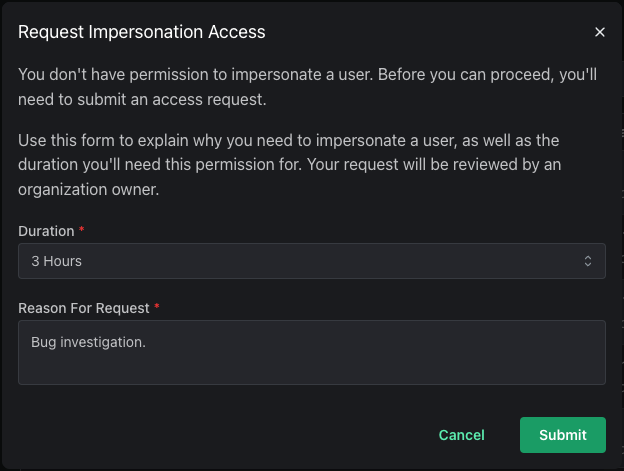
Members with the "Can Approve" permission will then receive an email alert of the request, as well as see an alert in the User Impersonation page in the PropelAuth dashboard. When viewing the request, they have the ability to adjust the duration and either approve or reject it.
The requester will receive an email once their request is approved or denied.
Impersonation Logs
The impersonation audit logs provides you with all the information you need regarding impersonation, including when a request is created, approved, denied, and when an impersonation session has started.
You can also filter these logs by event type, who caused the event, and by date.
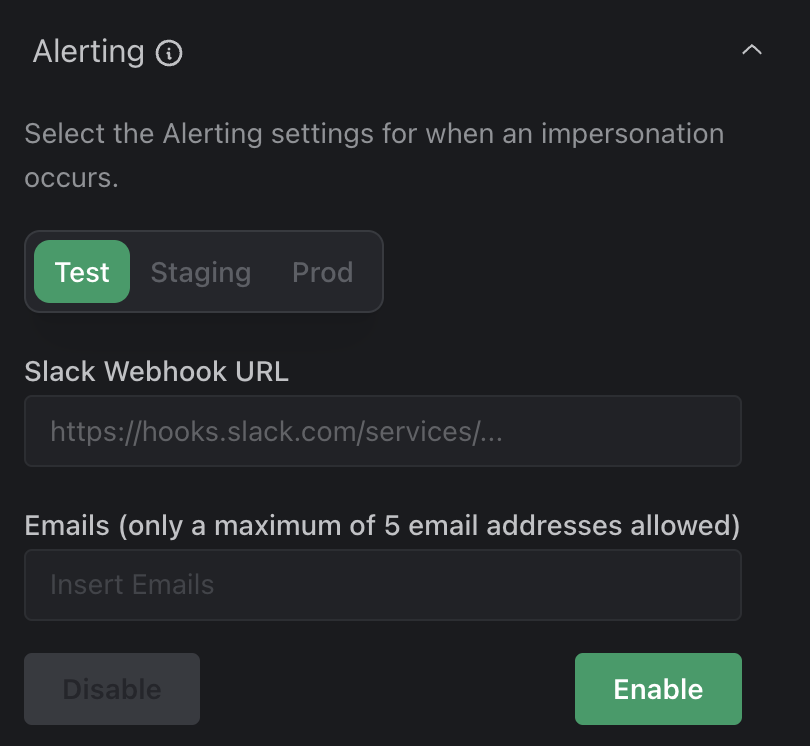
Alerting
If you would like to be proactively notified when one of your employees impersonates a user, you can turn on alerting. Alerting can be done via email or Slack and can be configured per environment.
Identifying Impersonated Users
When you (or someone on your team) is impersonating a user, they will be able to perform actions as that user, within your product. You may, for example, want to:
- Limit the actions that can be performed while impersonating a user
- Audit the actions that were performed while impersonating a user
- Limit the data that can be viewed while impersonating a user
- Add a banner to your product, indicating that the user is being impersonated
- To help you distinguish between a user and an impersonated user, there’s an impersonatorUserId field on the user object, in both the frontend and the backend. This field will be set to the ID of the person on your team who is impersonating the user, if any.
In the backend, you could use this field to limit the actions that can be performed while impersonating a user:
// Express example
app.post("/api/sensitive-action", auth.requireUser, (req, res) => {
if (req.user.impersonatorUserId) {
res.status(403).send("You cannot perform this action while impersonating a user")
} else {
// Perform the sensitive action
}
})
To fetch more information about your employee who was impersonating a user, use the Fetch Employee By ID API.
See the Reference documentation for more information about the library for your language/framework.
