Amazon S3 Audit Log Export
PropelAuth's Amazon S3 integration allows you to send Audit Logs about your users and organizations to your Amazon S3 buckets.
Set Up
Start by navigating to the Integrations page in your PropelAuth Dashboard and selecting Amazon S3 in the integrations list. Then, click on Add New Export Location.
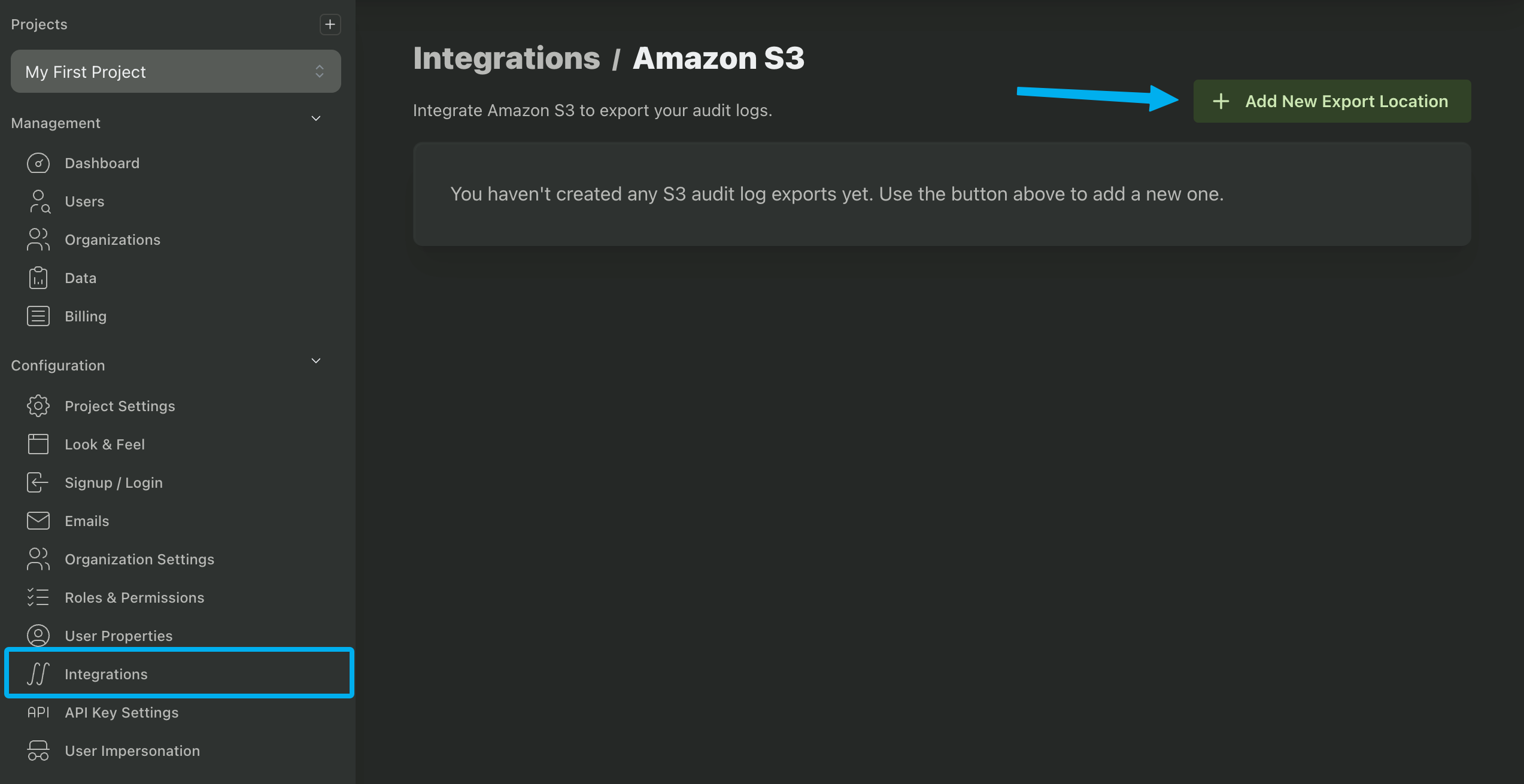
We'll need to collect five values.
- Navigate to S3 and create a new bucket. This bucket doesn't need to be publicly accessible, as we will be making credentials to write to it. Copy the name of the new S3 bucket into the Bucket Name field in PropelAuth.
- Next, we're going to create a policy that can write to this bucket. Navigate to IAM and create a new policy. When specifying the permissions, select JSON and copy this permission. Make sure to replace
{YOUR_BUCKET_NAME}with the name of the bucket from the previous step.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:PutObject",
"Resource": "arn:aws:s3:::{YOUR_BUCKET_NAME}/*"
}
]
}
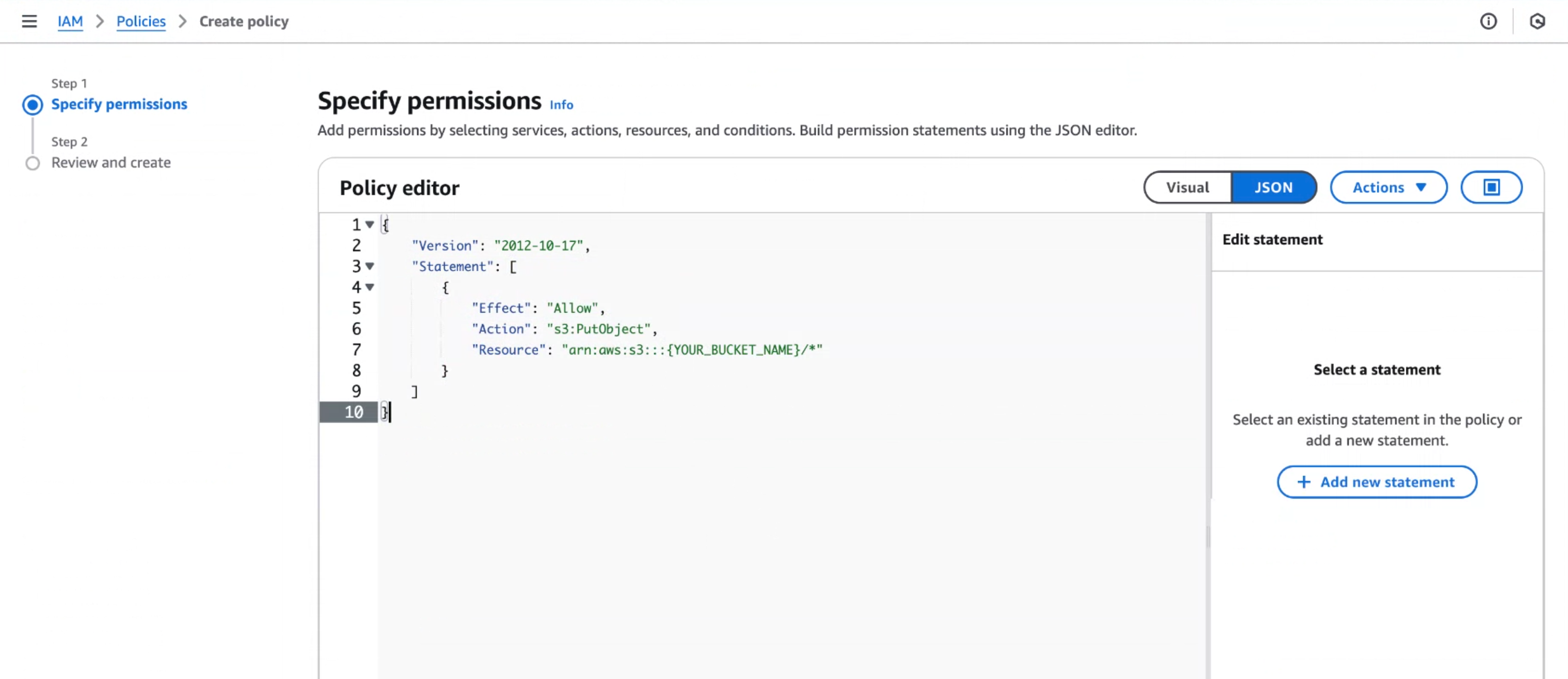
Continue with creating your policy by naming it. You do not need to change any of the default values.
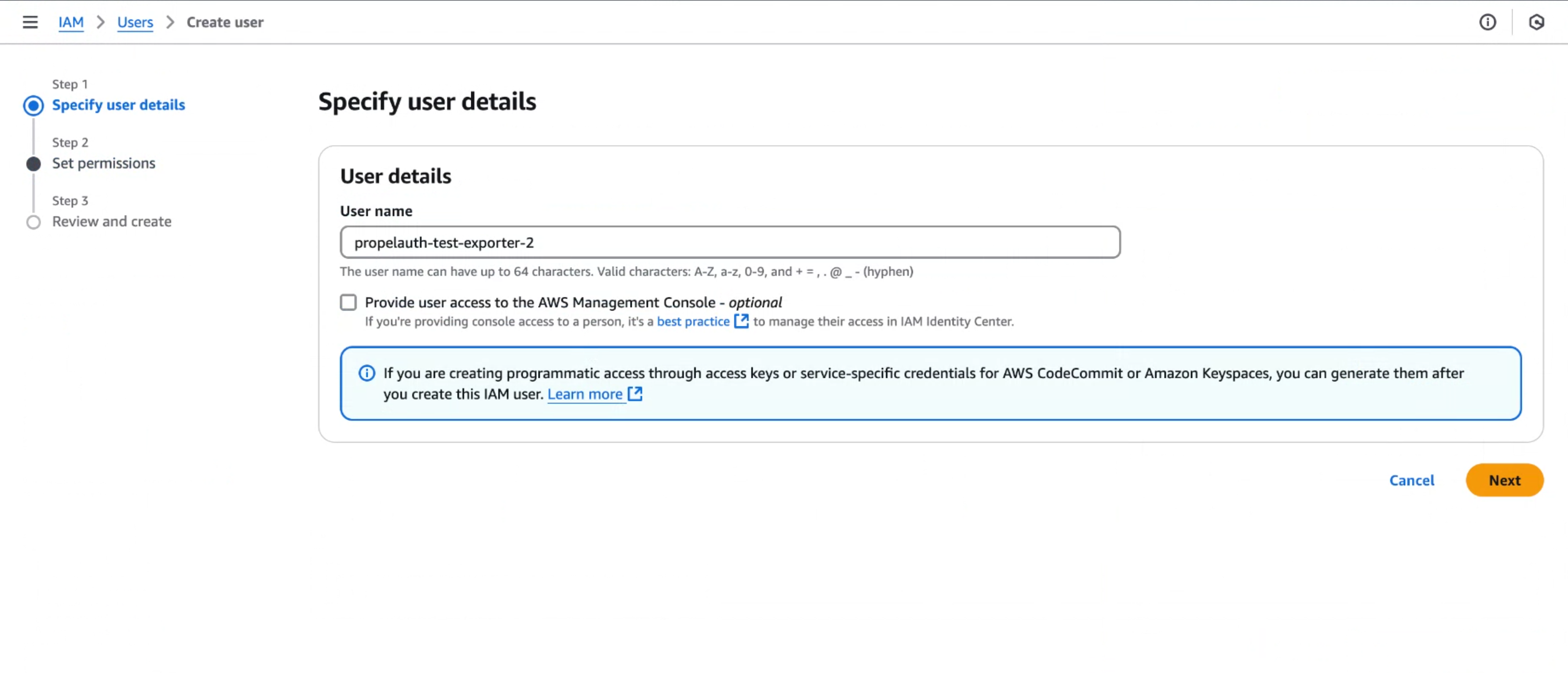
- Navigate to IAM and create a new user. Do not check “Provider user access to the AWS Management Console”.
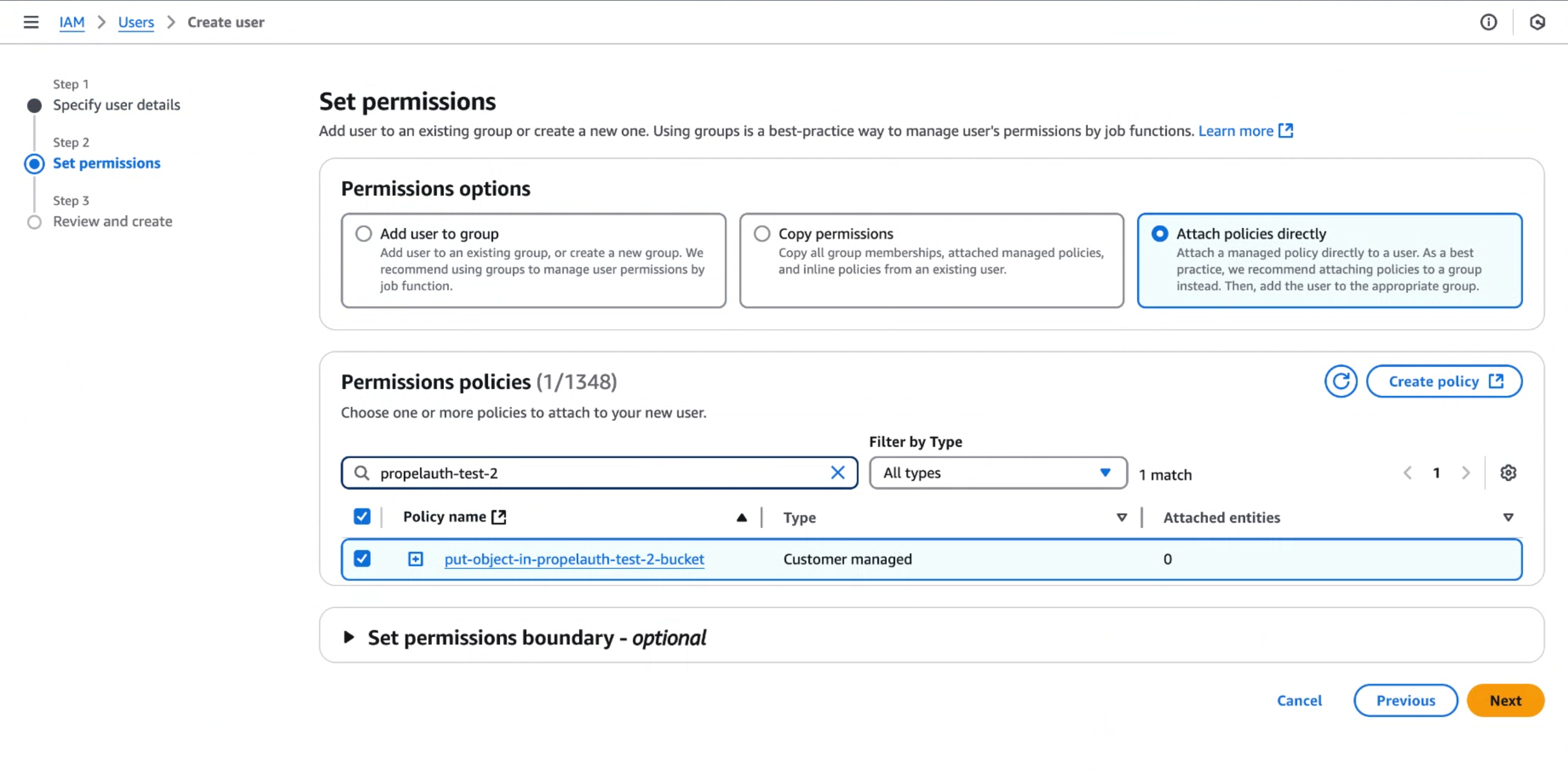
- Select Attach policies directly and add the policy you created in step 2. Create the user.
- Navigate to the new user and select the Security credentials tab. Then, Create access key.
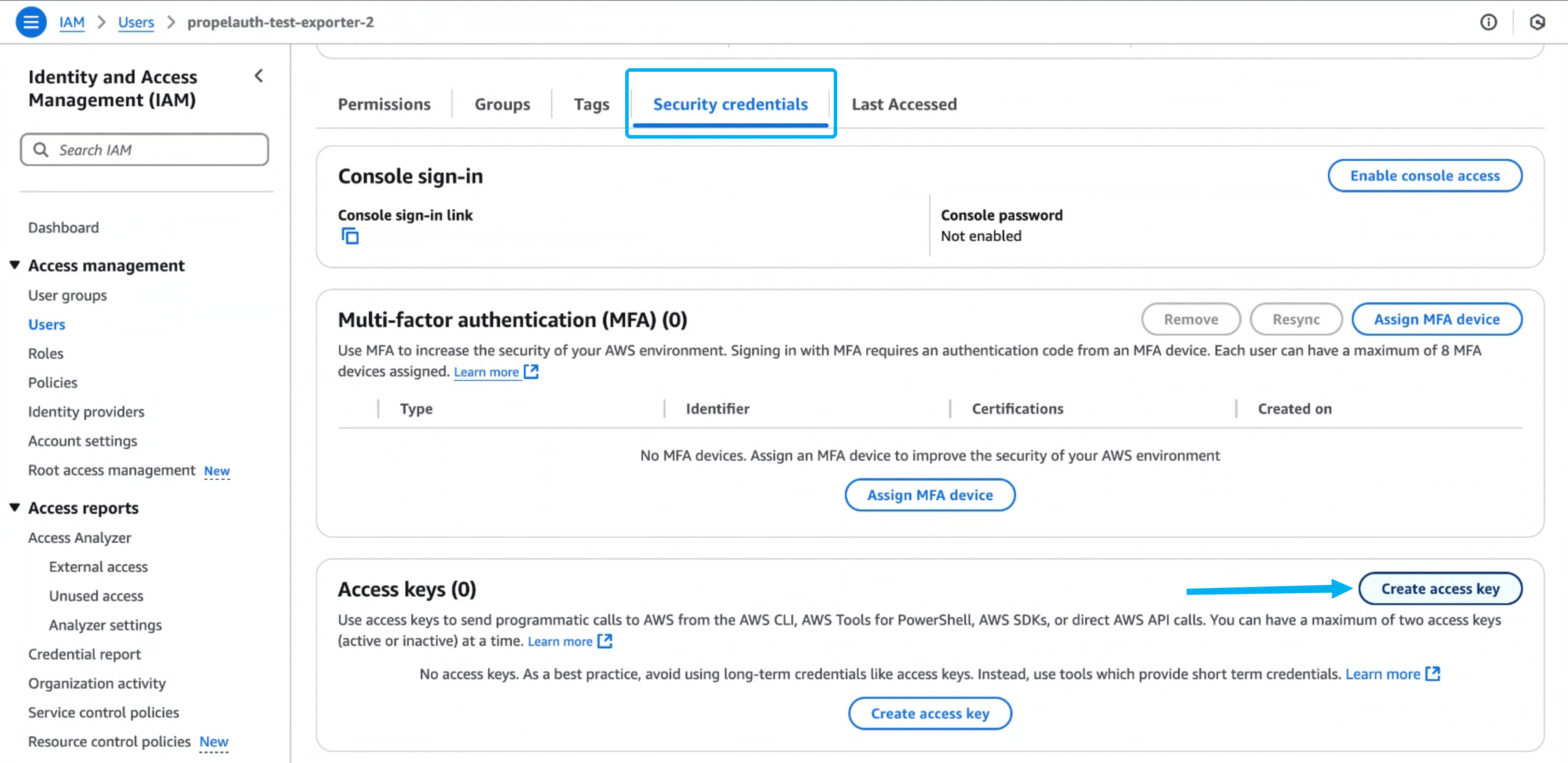
-
Select Third-party service, check the “Confirmation” checkbox, and click Next.
-
Copy the Access key and Secret access key into PropelAuth.
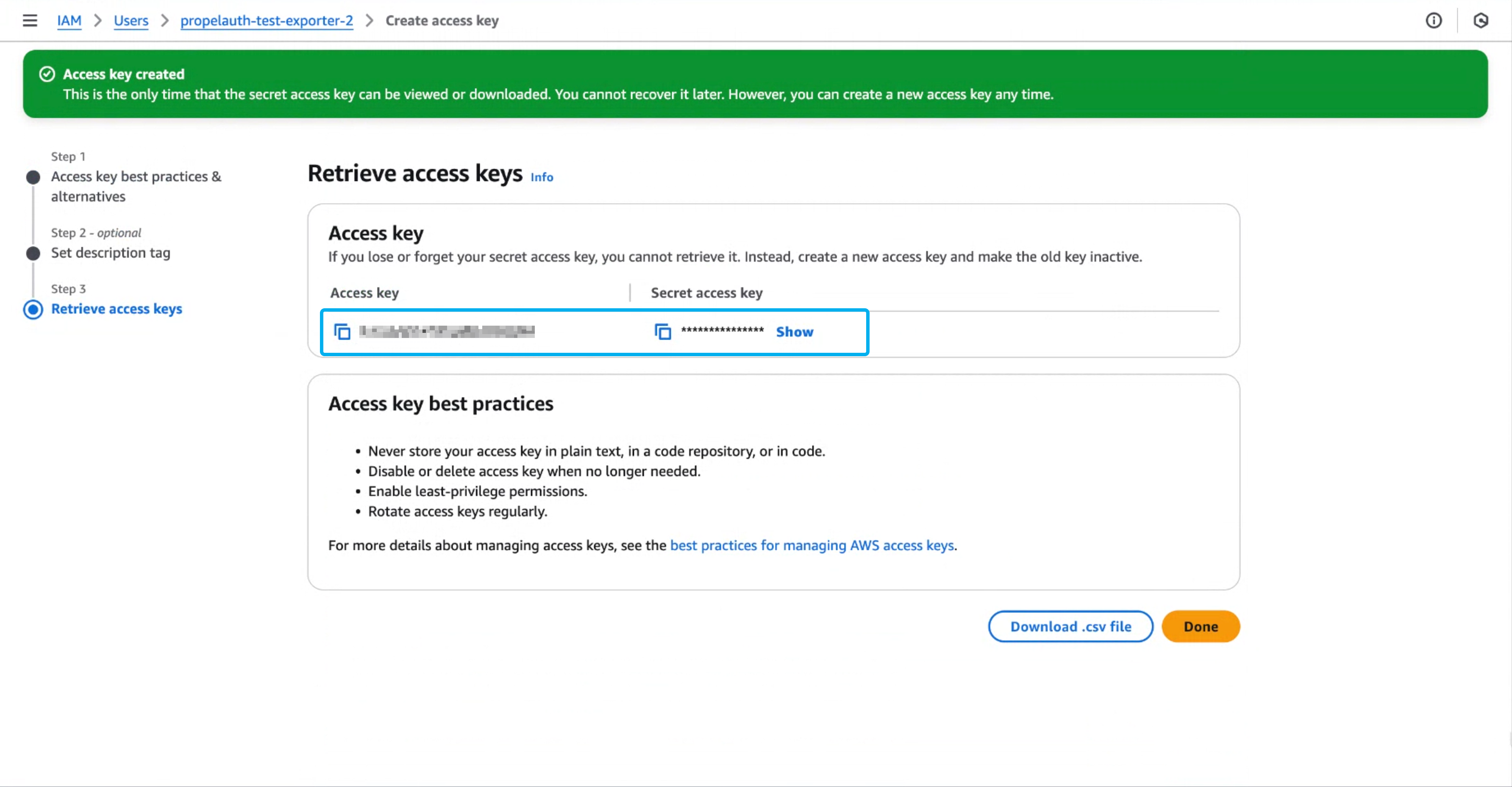
- Set your Region and Path values,
Choosing Event Filters
There are two main types of events in PropelAuth - User events and Org events. You can find a full list of these events in the Audit Log documentation.
By default, all User events and Org events will be sent to your S3 bucket. However, you can also choose to filter down to only include certain events.
Event Format
Once setup, PropelAuth will send a log in JSON format to your S3 bucket. Here is an example of what this can look like:
[
{
"id": "06dee7...",
"user_id": "255f9d...",
"user_email": "example_user@propelauth.com",
"org_name": null,
"event_type": "UserCreated",
"event_data": {
"UserCreated": {
"email": "example_user@propelauth.com",
"email_confirmed": true,
"first_name": null,
"last_name": null,
"picture_url": null,
"properties": {},
"username": null
}
},
"created_at": 1745598561,
"caused_by_id": "cd7c3d0...",
"caused_by_type": "Employee",
"caused_by_metadata": {
"email": "example@propelauth.com"
},
"caused_by_source_ip": "1.1.1.1",
"caused_by_user_agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/135.0.0.0 Safari/537.36",
"impersonator_id": null,
"impersonator_metadata": null
}
]
