Login Methods
By default, your project starts with password authentication. At any time, you can simply enable or disable password, passwordless, social login, or Single Sign-On (SSO) options within your dashboard — no code modifications needed.
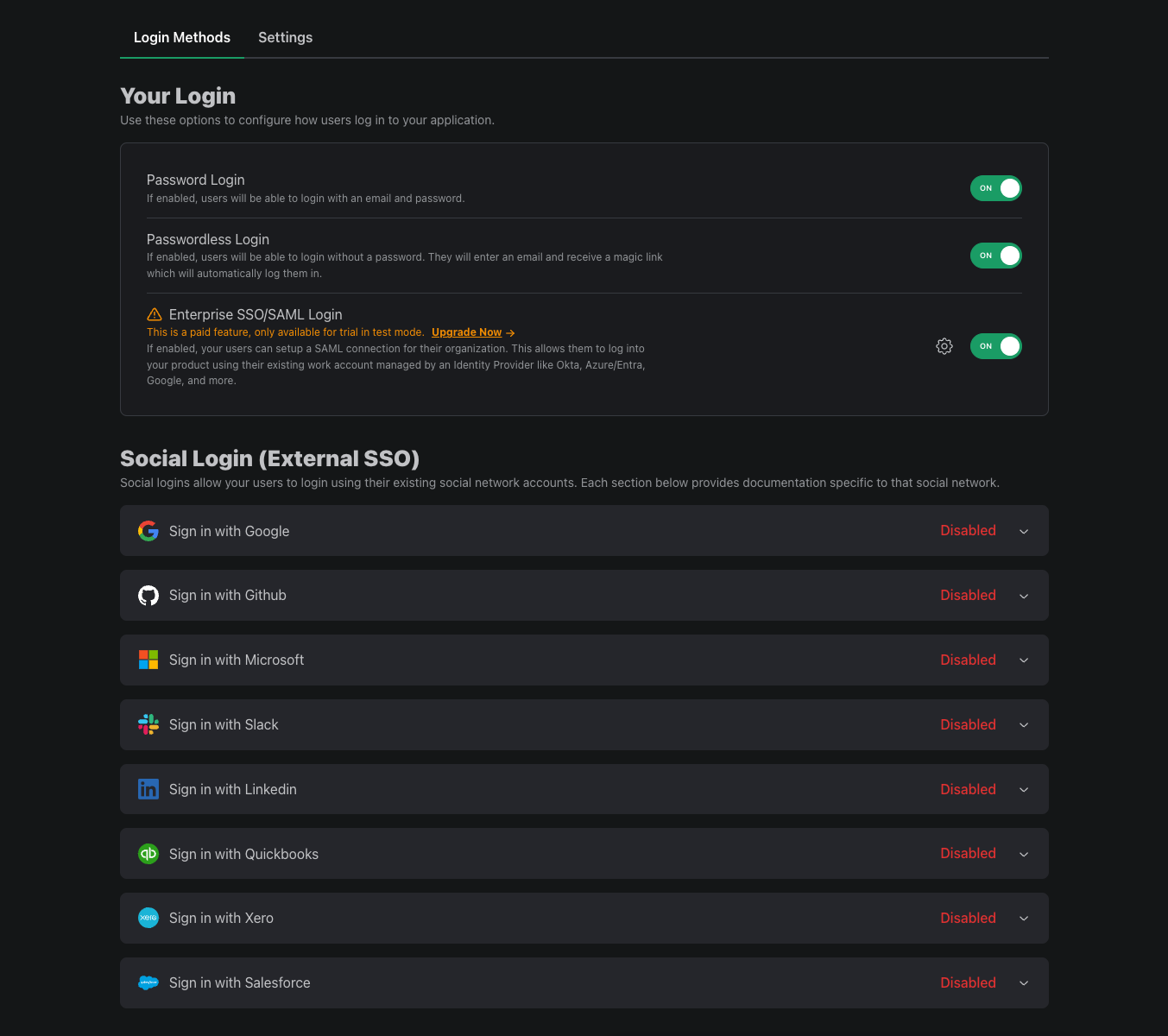
Passwords
A classic login method, passwords are the most common way for users to sign up and log in to your app.
By default, we add extra security for your users by disallowing them from using common passwords. We also protect you from brute force attacks by limiting the number of failed login attempts.
Our default password policy is that we require >= 8 characters and a password that hasn't been in a previous breach. This (and two-factor authentication (2FA) available to everyone) matches the NIST recommendation for passwords.
If a user forgets their password, no problem. We handle the password reset flow with hosted pages and transactional emails - both of which are customizable.
Customize Password Requirements
You can customize your password requirements by length as well as the minimum number of uppercase characters, lowercase characters, digits, and special characters. You can also disable our added security of disallowing common passwords.
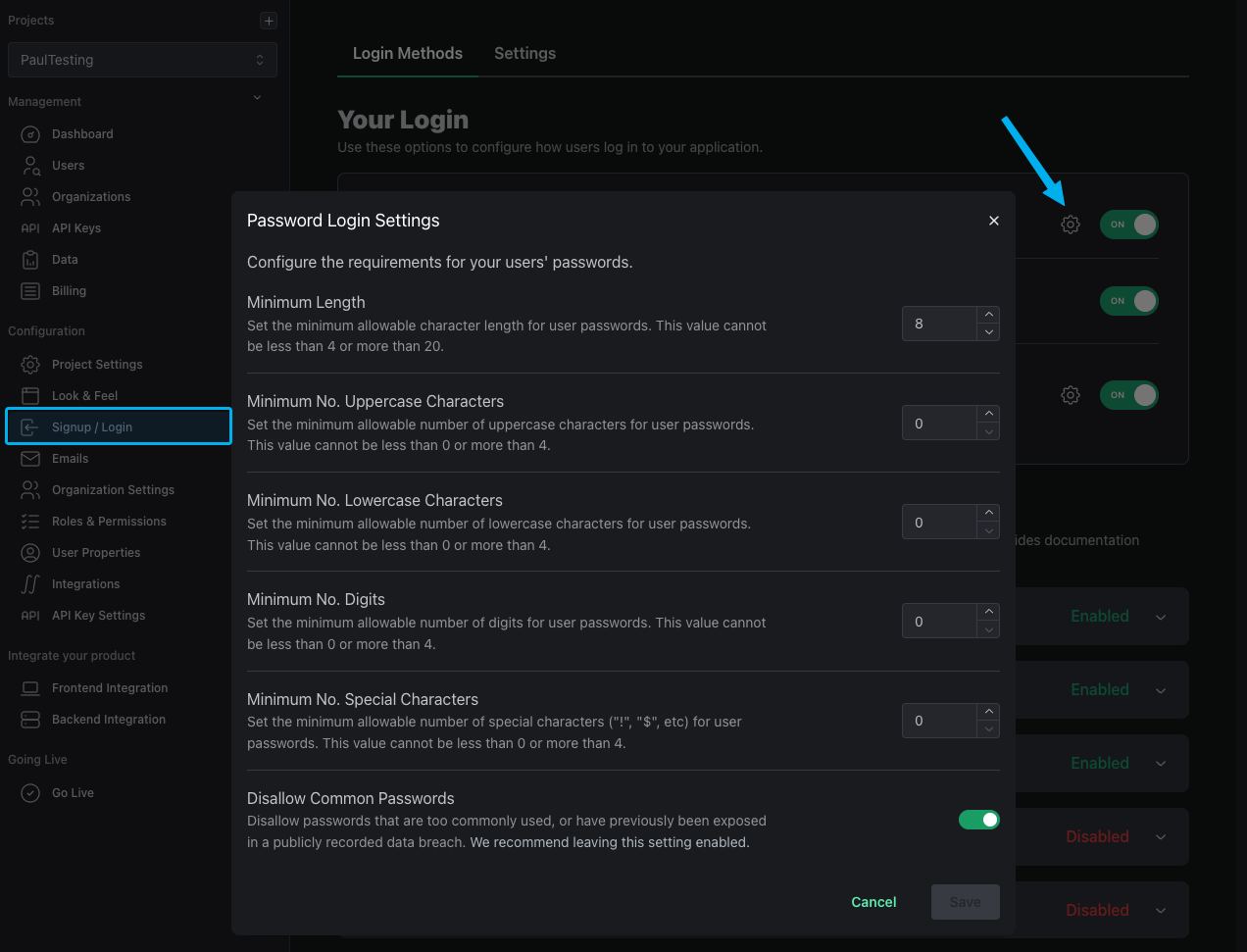
To customize your password requirements, head to the Signup / Login page and click the cog next to Password Login.
Enforce Password Rotation
PropelAuth supports enforcing password rotation at the organization level. When enabling the setting for an organization, you can specify the number of days in a rotation period (how often users must change their password) as well as the password history size.
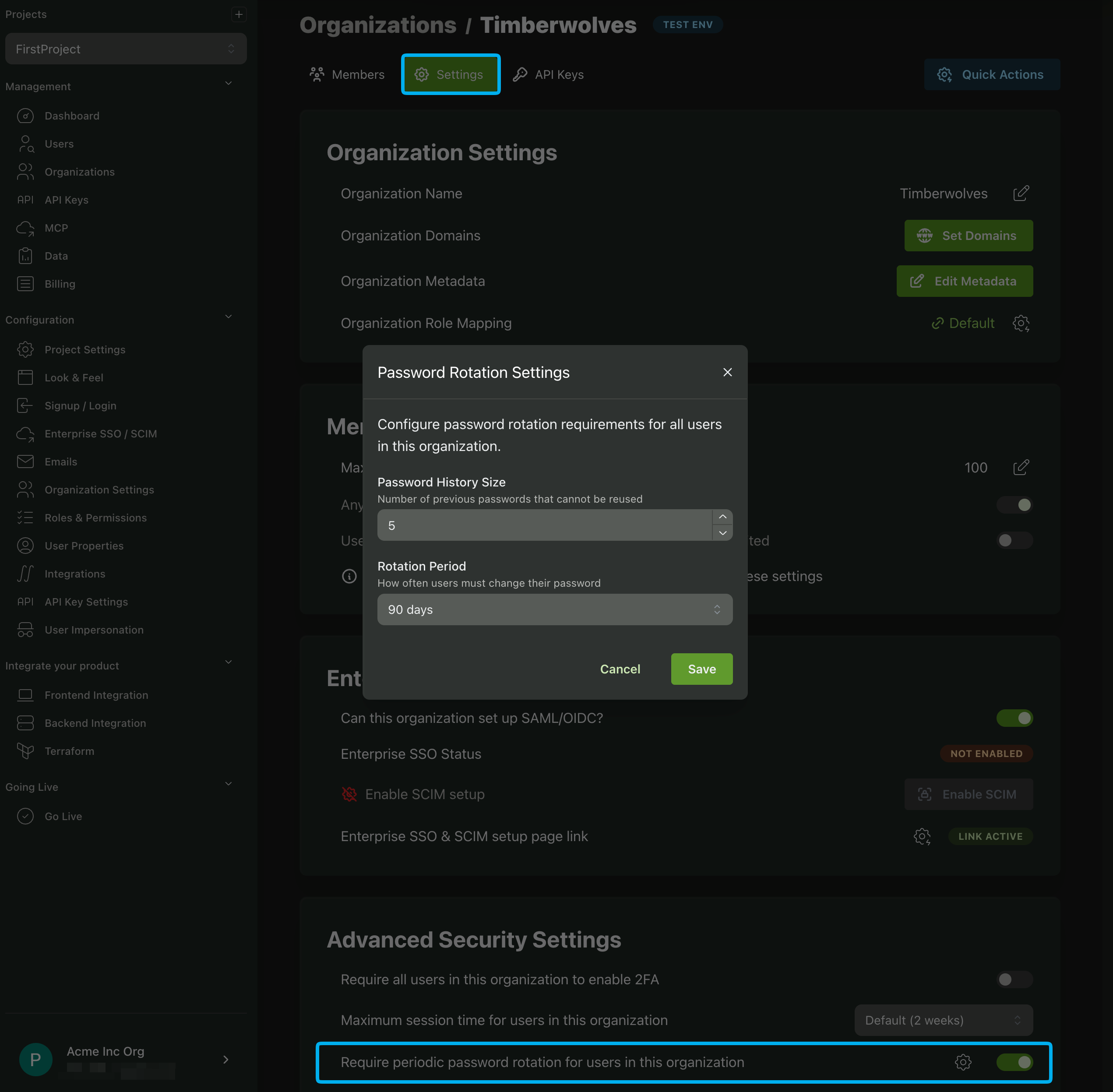
You can enforce password rotation by navigating to an org's settings page, scrolling down to the Advanced Security Settings section,and toggling the Require periodic password rotation for users in this organization setting.
Lockouts on Failed Attempts
PropelAuth supports locking user accounts after too many unsuccessful login attempts. The exact amount depends on the length of time between requests, but roughly 10 incorrect attempts will result in a locked account.
If a user's account becomes locked, we will automatically send them an email notification explaining the situation and providing instructions for unlocking their account. If you would like to be notified when a user's account is locked you can subscribe to the user.locked webhook event.
Passwordless / Magic Links
Passwordless authentication allows users to log in without a password. This is done by sending a login link to the user's email address.
We can manage the entire process for you through our hosted login page, including sending the email and verifying the one-time password. By default, the link will expire in 2 hours but you can configure this by updating the email link expiration setting.
If you would rather handle it yourself, you can use our API to create a magic link that a user can use to log in. This allows you to customize the expiration and the location the user is redirected to after logging in. Note that this doesn't send the email to the user, it just generates and returns the URL.
If you'd like to send emails from your own domain, check out our transactional emails docs or email us at support@propelauth.com and we'll help get you set up.
Customize Magic Link Settings
You can customize the default behavior of magic links in your project by navigating to the Signup / Login page, clicking on Settings, and then selecting the Configure Magic Link Settings button.
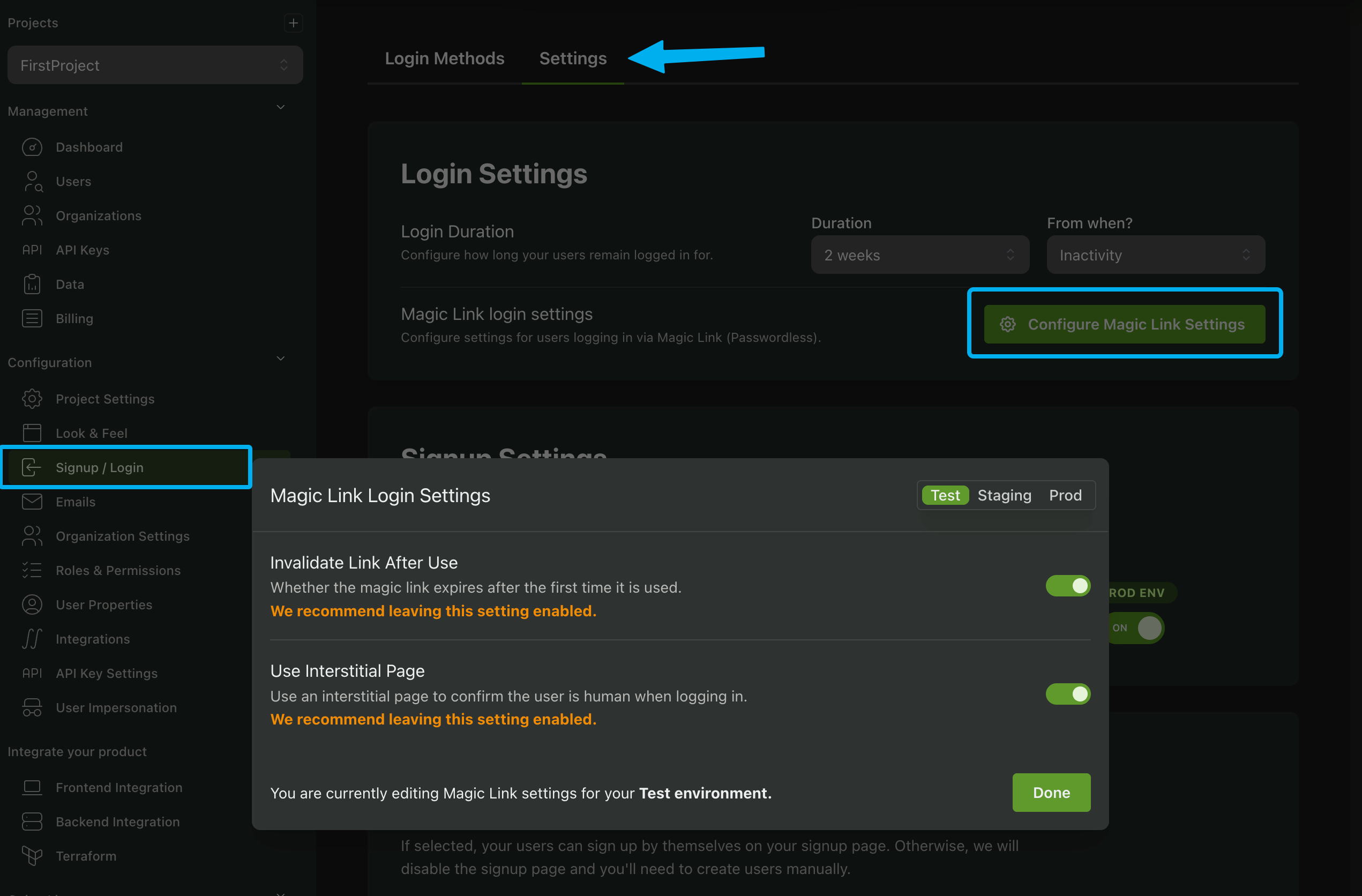
-
Invalidate Link After Use: When enabled, this setting ensures that once a magic link has been used for authentication, it cannot be reused. This adds an extra layer of security by preventing potential misuse of the link. It is important to note that some email clients may prefetch links, which could inadvertently invalidate the link before the user has a chance to use it. Consider this behavior when deciding whether to enable this option.
-
Use Interstitial Page: When enabled, users will be directed to an interstitial page after clicking the magic link in their email. This page provides a brief confirmation message before redirecting them to the final destination. This can enhance the user experience by providing clarity on the login process as well as an additional security step.
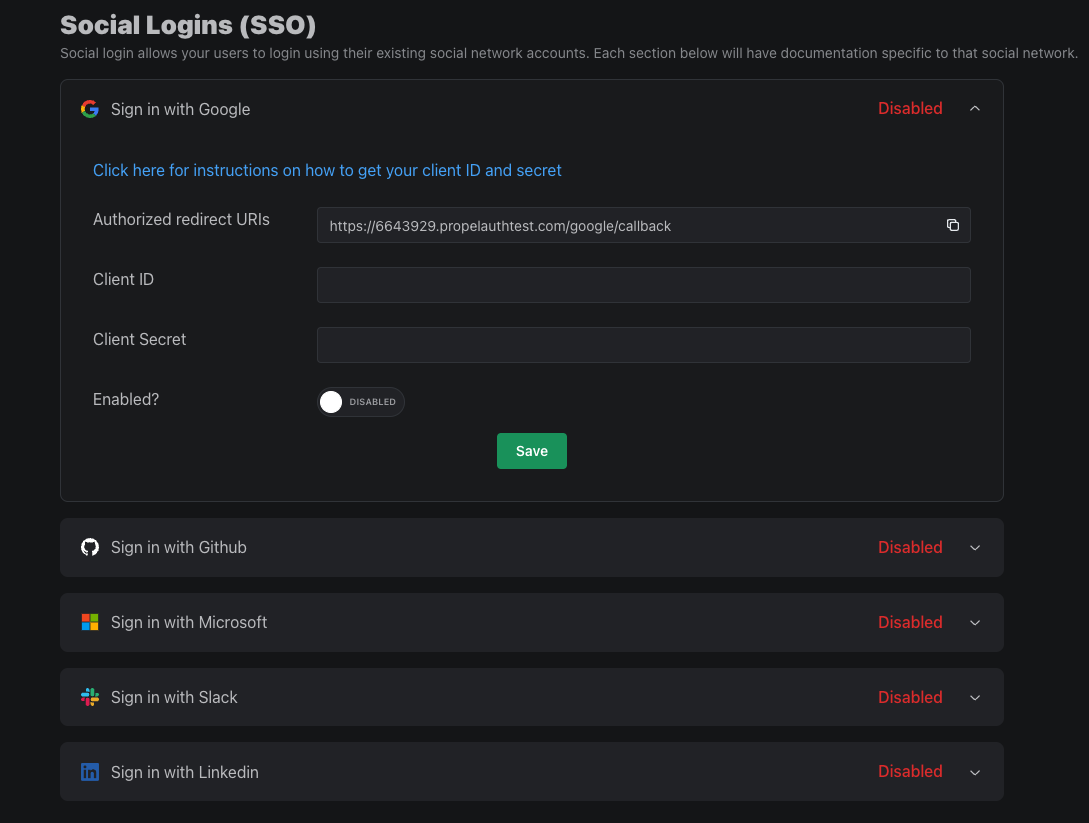
Social login / SSO
Social login / SSO allows your users to login using their existing social network accounts (e.g. Google, Github, Microsoft). It makes signing up simpler for your users, as they don't have to remember a password.
Enabling social logins with PropelAuth is a breeze since the majority of the work is done by your hosted authentication pages.
Instructions for enabling Social login are dependent on the specific social network you want to integrate with. Click here for a full list of providers with instructions.
If a user signs up with a social provider after signing up with their email address, their accounts will automatically be linked.
Additionally, if a user creates an account with Google SSO and then later with Github, for example, those accounts will be linked if the emails tied to the two match.
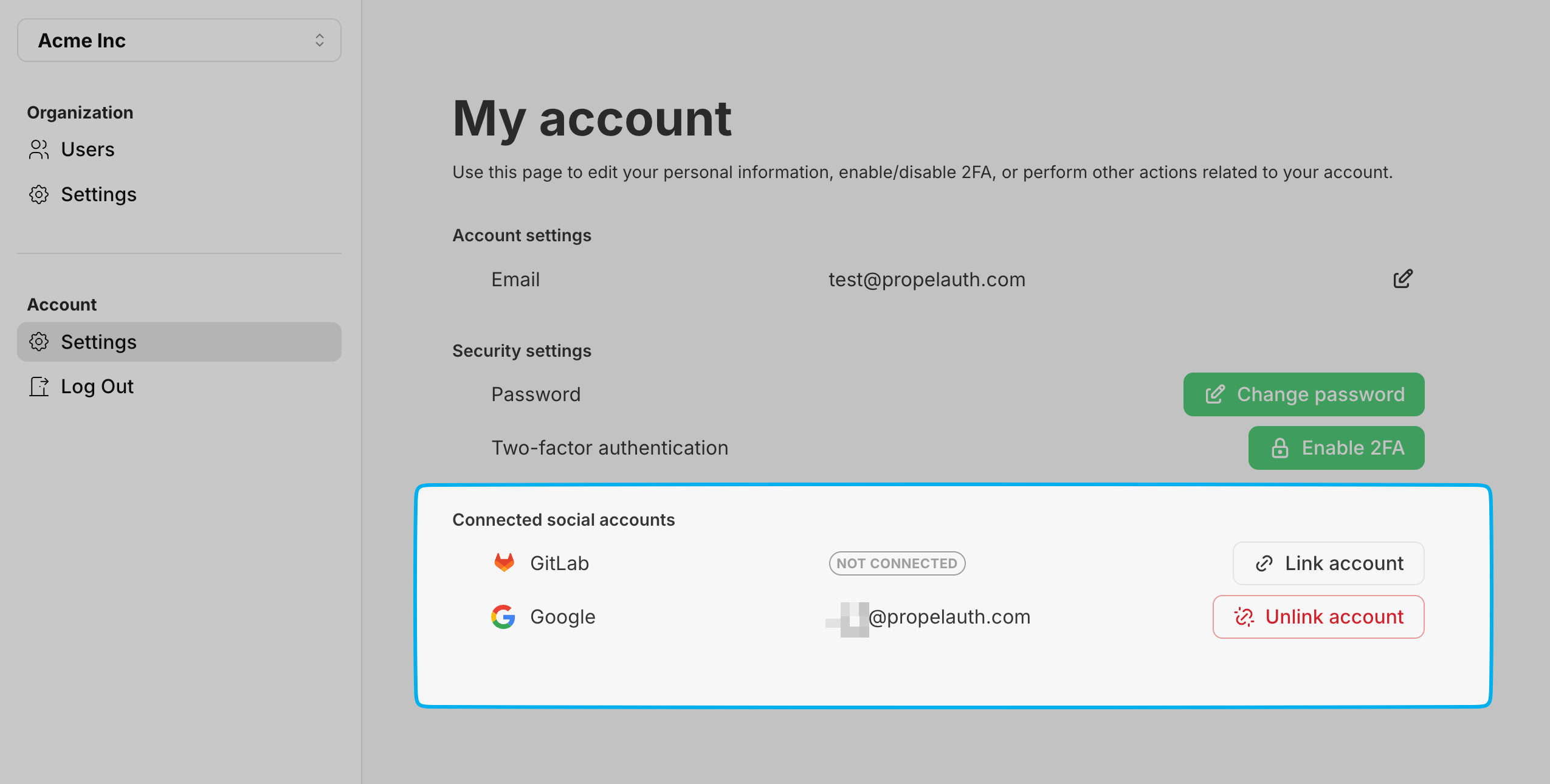
Social Account Linking
Social Account Linking allows users to connect external social accounts to their existing user account through the User Account Page, even when the social account uses a different email address. This feature is useful if a customer logs in with their work address but then wants to link their personal social account, such as LinkedIn or Google.
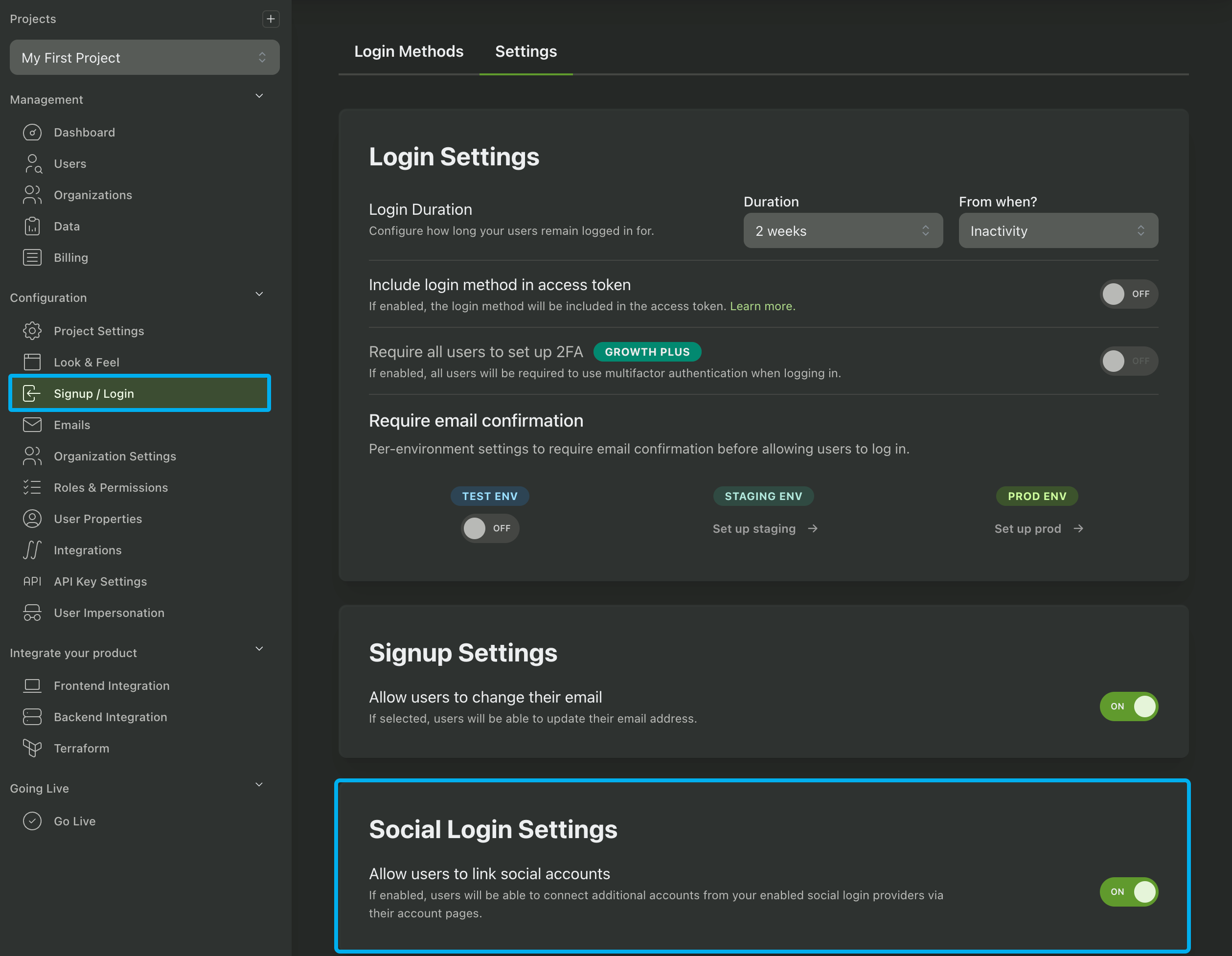
To enable Social Account Linking, navigate to the Settings tab in your Signup / Login page and enable the Allow users to link social accounts setting.
A user can then navigate to their User Account Page to link external social accounts. Alternatively, you can redirect the user to {AUTH_URL}/api/fe/v3/{provider}/link to send them directly to the provider's login flow. Click here for more information.
If you're wanting to get the user's access token for the social provider, you can do so by using the Fetch User OAuth Tokens endpoint.
Enterprise SSO (SAML / OIDC)
Enterprise SSO (SAML/OIDC) allows your users to login using their existing enterprise accounts (e.g. Okta, OneLogin, Entra ID).
It's often a requirement for enterprise customers to use their existing enterprise accounts to login to your app.
We provide self-service UIs for your customers to set up their own Enterprise SSO connections. You can read more about PropelAuth's Enterprise SSO support here.
Restricting Login Methods
If you have multiple login methods enabled but want to show only specific login methods to some users, you can do so via the opt_hint query parameter. For example, if you only want your users to login via email/password, you can send them to:
{AUTH_URL}?opt_hint=pw
If you want to offer them two login methods, simply add a comma between values:
{AUTH_URL}?opt_hint=pw,pwl
Here is a full list of possible values for the opt_hint query parameter.
- Email/password =
pw - Passwordless =
pwl - SSO =
sso - Google =
gl - Gitlab =
gb - Github =
gh - Microsoft =
ms - Slack =
sl - LinkedIn =
li - Atlassian =
at - Apple =
ap - Quickbooks =
qb - Salesforce =
sf - Xero =
xr - Salesloft =
slf - Outreach =
ot - OTP =
otp
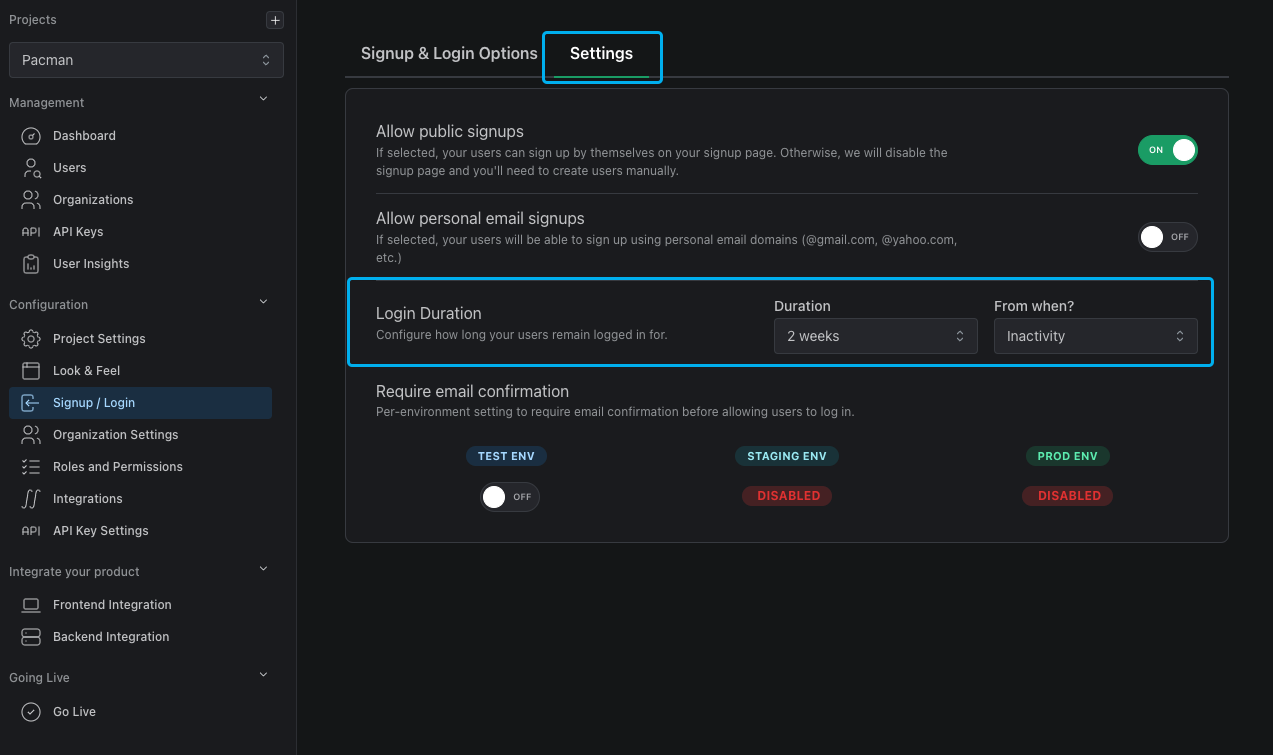
User Login Duration
You can control how long users stay logged in for in your dashboard. You can choose between your users staying logged in for a fixed amount of time or having them stay logged in as long as they remain active.
Prefilling the Email Field
If you would like to prefill the email field when redirecting a user to your login page, you can do so by using the e query parameter and base64 encoding the user's email address.
For example, you can redirect them to:
{AUTH_URL}/login?e=dGVzdEBleGFtcGxlLmNvbQ==
This will automatically populate the email field with "test@example.com".
Controlling Who Can Signup
PropelAuth offers multiple methods to control who can or cannot access your app. These settings can be found in the settings tab in your Signup / Login page.
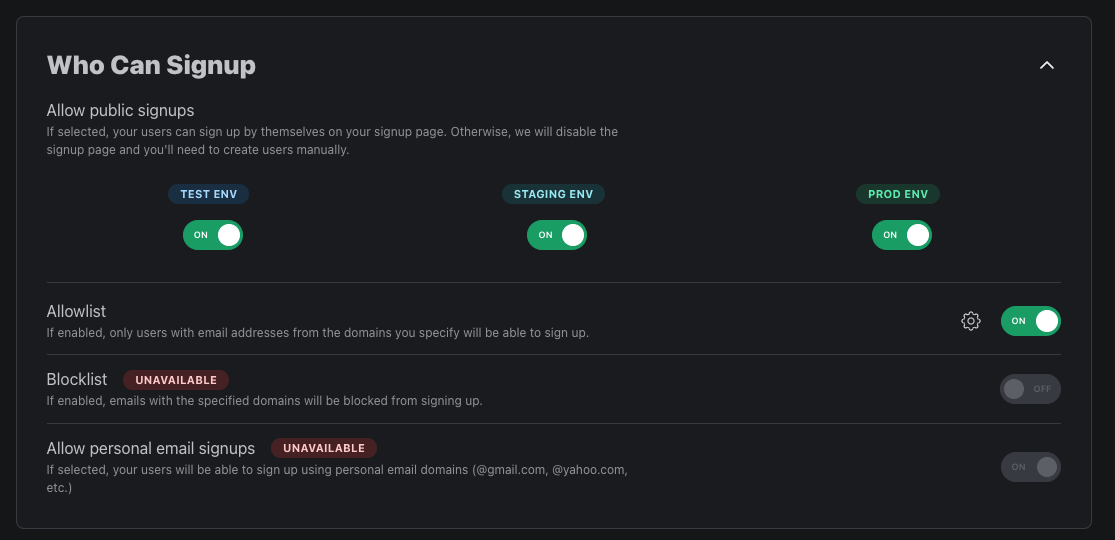
Disable Public Signups
For each of your environments you have the ability to enable or disable public signups. If disabled, there will no longer be a signup page for that environment. However, users with the invite other users permission can still invite users to their org. You can also invite users manually to your application in the Users page.
Disable Personal or Disposable Emails
You also have the option to enable or disable signups with personal emails. If disabled, users with common personal email domains (@gmail.com, @yahoo.com, etc.) will not be able to signup for your app.
You can also block disposable email addresses from signing up for your app. If enabled, users trying to sign up with a disposable/temporary email address (from services like Mailinator, 10MinuteMail, etc.) will be restricted from signing up.
Allow or Block Domains from Signup
If you want more control over who can signup for your app, the allowlist and blocklist feature allows you to create a list of domains to either allow access to or restrict from signing up for your project. The list of domains you provide must be pipe-delimited, for example:
example.com | example2.org | example3.gov
Block Common Spam IP addresses
To further protect your application from spam signups, you can enable the option to block common spam IP addresses. When this setting is enabled, any signup attempts originating from known spam IP addresses will be automatically blocked, helping to maintain the integrity of your user base.
You can enable this setting by navigating to the Settings tab in your Signup / Login page and toggling on the Block IPs associated with spam option.
